FUCKING BRUTALIZING Windows Security/Microsoft Defender in Windows 10 and 11
If I wanted bitching about my pirated software, I'd be using a Mac.
If you're just looking for how to do this, scroll down. I have a real damn good tendency to go off on a tangent in text. But if you're some retard that downloads random cracks off the Internet you probably shouldn't follow this and just purchase your software through legal(ly questionable) means.
So you pirate software right? I can count the number of software licenses I have on a single hand, 3 or 4 of them is Windows keys I bought off eBay for cheap. Anyways, have you ever used a crack, keygen, or loader? Those are the ways that software protection is bypassed (short of just giving some key you bought with fake details inside the release).
Sadly, antivirus and antimalware vendors seem to look the other way at how beneficial software piracy is to your wallet. Some software companies are in kahoots with the security vendors to shitlist cracks of their software. But usually what happens is the obfuscation (VMProtect), packing (UPX) or patch creator itself (diablo2oo2's Universal Patcher) ends up being used by bad actors for malicious cracks or straight up just horrifying shit, leading to the signatures for generic variants to get shitlisted, and software creators that legitimately use the shit has to usually go through the vendors and ask them to either whitelist their code signing signature (not likely) or submit each file to be individually whitelisted (likely, how much software have you seen with signed binaries?).
Now usually I'd support this being in-place for idiots. Like, I used to have some classmates that would download cracked/trained games and use shady versions of Lucky Patcher back when it was a thing that people gave a shit about. Those people shouldn't be running pirated software because they're fucking stupid and need protection of their computer being used for some virgin's botnet. But, I should be able to disable the fucking thing right? Well...
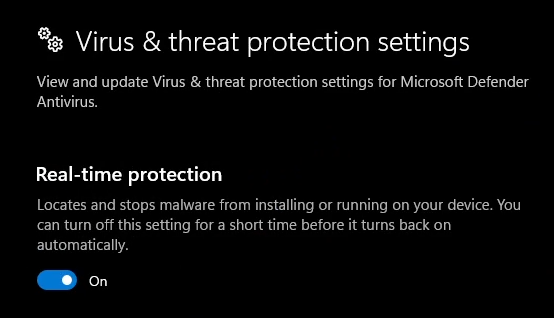
This is the button that is officially how you disable it. Something you'll notice though is "You can turn off this setting for a short time before it turns back on automatically." That's a fucking "let me test this shit rq" disable button.
But, there's an official way for domain administrators, located in Group Policy:
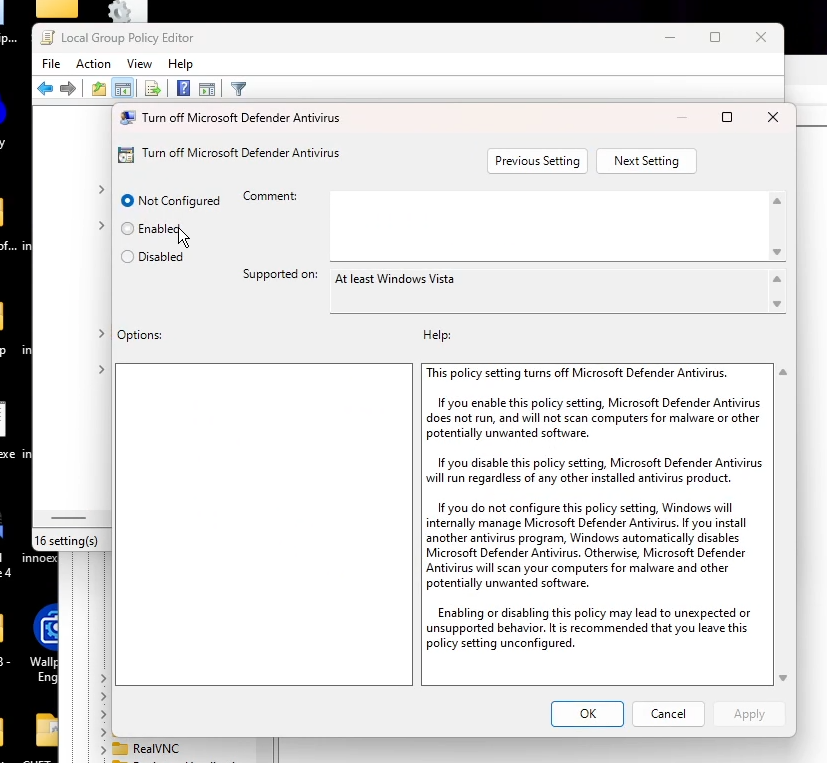
But, that's how I disabled it. And the setting just reset itself back to "Not Configured" (read: Disabled) after a reboot. I find this out after loading some shit up after a reboot and...
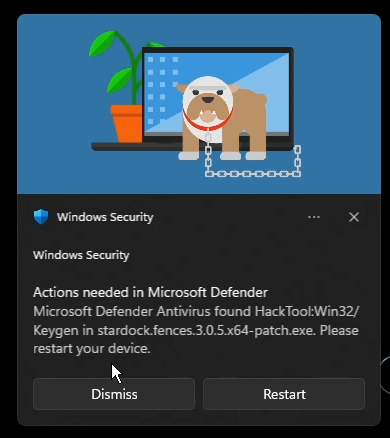
Fuck you vile bitch, let me run this "HackTool:Win32/Keygen"!
So, how do you disable this shit and fucking lock it from disabling itself, you know fucking BRUTALIZING it? Registry Editor, my friend.
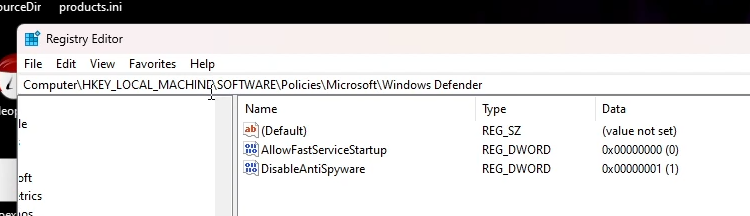
Run the Registry Editor (regedit.exe) from the Start Menu (Run dialog) and hit up HKLM\SOFTWARE\Policies\Microsoft\Windows Defender. Create a new "DWORD (32-bit) Value" named "DisableAntiSpyware" and set it to 1 in base hexadecimal. Might as well create another one called "AllowFastServiceStartup" and set it to 0, that'll make sure the fucker doesn't run at high priority when you turn your shit on.
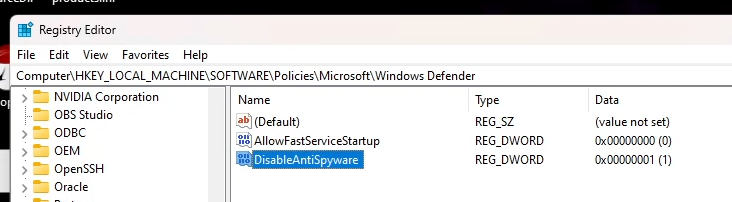
Now for the fun part, making sure it won't end up deleting that shit!
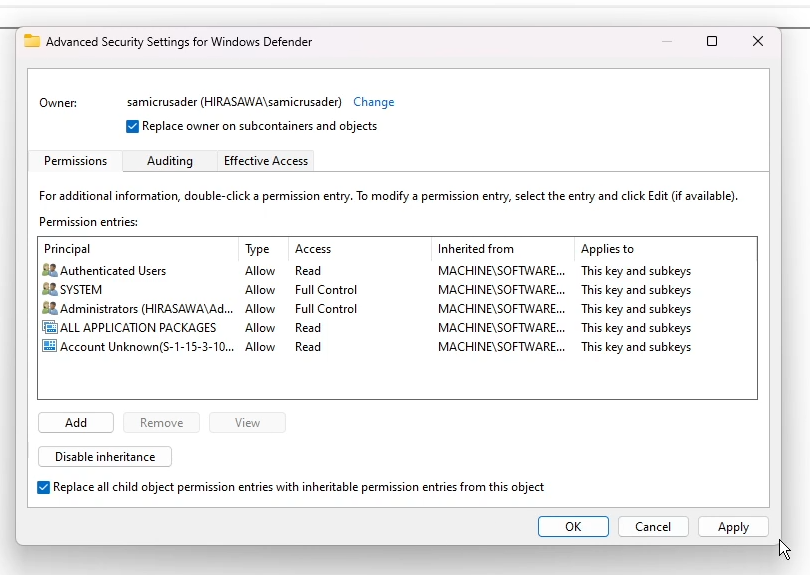
Right-click on the "Windows Defender" key in the left bar, select "Permissions". Click Advanced, in the advanced security window that pops up click "Change" under "Owner". Type in your Windows username and click "OK". Then, make sure to tick "Replace owner on subcontainers and objects" and "Replace all child object permission entries with inheritable permission entries from this object".
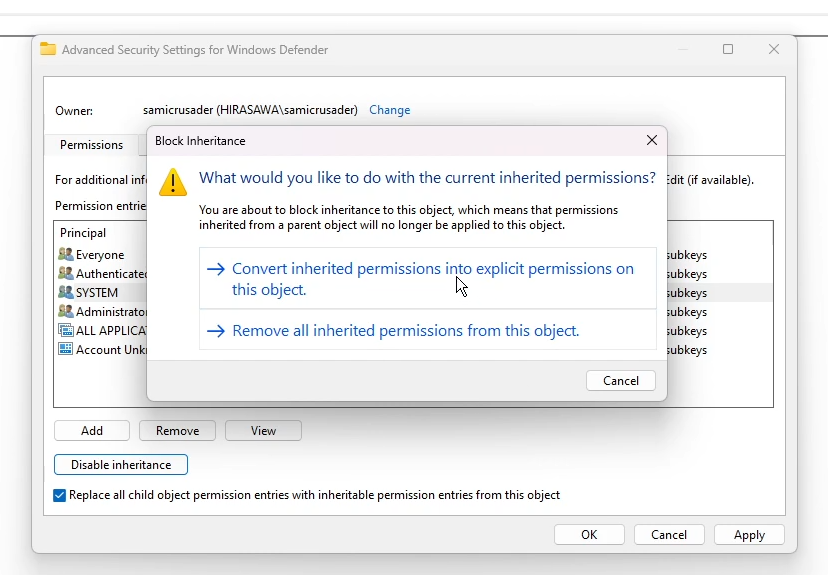
Click "OK", close the existing permissions window, and then re-open it. Click "Advanced" again. Now, click "Disable inheritance". When it asks you what the fuck to do with the current ones, just click "Convert inherited permissions into explicit permissions on this object."
Now, back in the advanced security settings window, edit EVERY "Permission entry", showing advanced permissions, disabling the following permissions:
- Set Value
- Create Subkey
- Create Link
- Delete
- Write DAC
- Write Owner
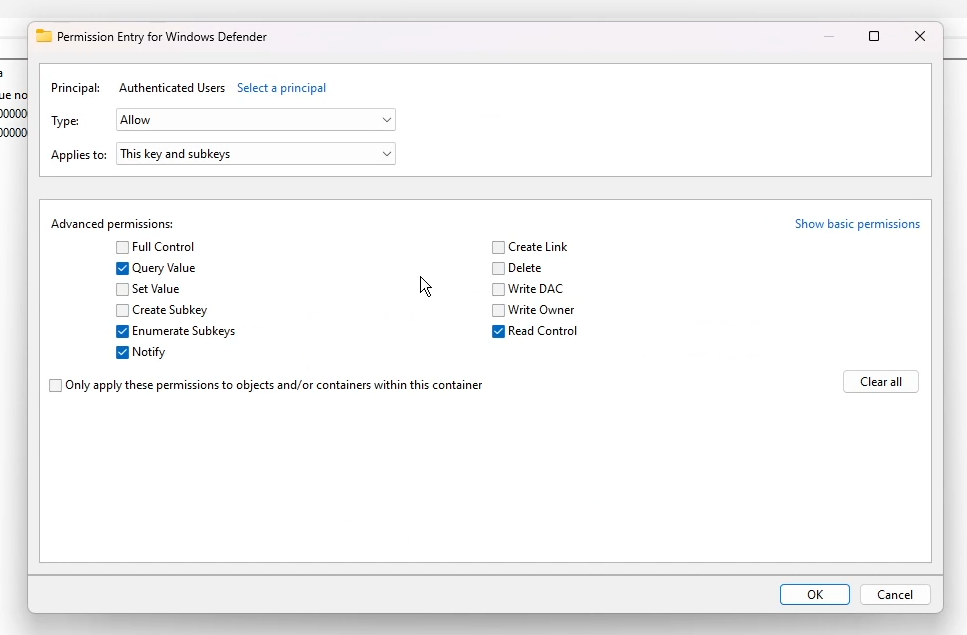
Leave "Full Control" alone, it'll untick itself. After applying these to each entry, click Apply, then OK. If you re-open Windows Security...
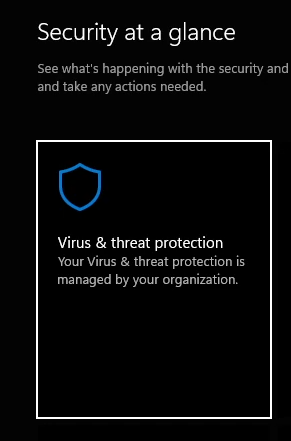
Now for the ultimate test. Rebooting and seeing if it persists.
So? Well...
But for the real test...
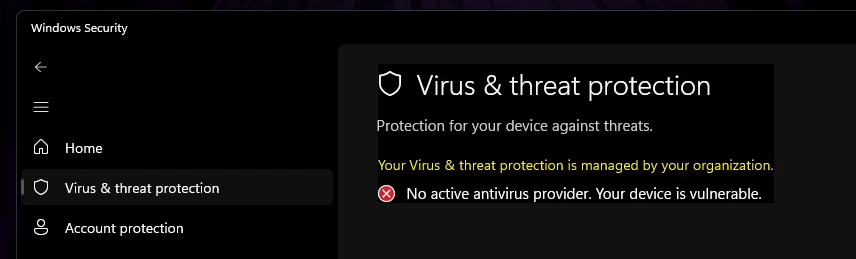
My reaction to this information:

